As a business owner, it’s important to always keep your data security in mind. Having a safe and strong backup is necessary to keep your business away from cyberattacks and other inevitable cases that can cause you to lose files. In this case, you need a reliable IT support provider in Manhattan to help you transition to the cloud, which can help you safeguard your data.
- General Inquiries: 646-741-1800
- Service: 732-305-2434
Blog
Take Google Search to the next level
Google has become so popular that its name is actually a verb in the dictionary. Despite people using Google every day, many don’t know that the search engine’s simple-looking interface is chock full of features that’ll help you find information faster. Include and exclude keywords Google will understand most of the search terms you type […]
Managed IT Services in NYC Eliminate Many Operational Expenses

Work Anywhere, Anytime
Managed IT services providers in NYC offer cloud computing solutions which allow businesses to limit expenses while retaining productivity, service delivery, and outward expansion. There are several ways cloud computing makes this possible:
Reduced restrictions on software
Improvement of customer experience
Performance enhancement
Increased scalability
Reduced Restrictions
When you've got internal solutions that don't rely on cloud-based solutions, software applications must be consolidated to a single platform.
How will AI impact internet telephony?
Artificial Intelligence (AI) brings to mind robots that can perform tasks and think like human beings. While that’s certainly possible in the future, AI today is simply an intuitive set of technology that automates business processes. It’s been around for decades, and now it’s poised to make significant improvements to VoIP technology. Contact Center Operations […]
Why You Need IT Support in New York to Guarantee Data Safety

Data and efficient data management is crucial for running a successful business. Protecting your data determines, to a large extent, the continuity of your business venture. In some cases, you may need to partner with IT support firms in New York to guarantee the safety of your data and other IT resources.
Beware Of Apps Bundled With Your Windows 10
Have you recently purchased new laptops or computers? Don’t get too excited. A new report proves that pre-installed software such as free trials and web browser toolbars can pose high-security risks. So if you want to maximize your new investment, here are some things you might want to know: Tavis Ormandy, a researcher from Google’s […]
Why Managed IT Services in New York Should Include Cloud-Based Healthcare

Healthcare facilities require robust managed IT services in New York in order to meet HIPAA regulations and patient expectations. One way for hospitals to cut costs is to use subscription-based cloud services. Leaders in global healthcare cloud computing include Amazon Web Services, General Electric, IBM, Oracle, and Salesforce.
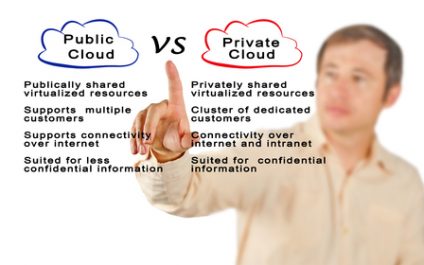
IT Support in New York & New Jersey: Public Cloud Vs. Private Cloud
Office 365 Update: New Tools You Need To Know
Yet again, Microsoft has released new AI-based features for Microsoft Excel, Word, Outlook, and more — a continuing trend since 2016’s launch of the Microsoft AI and Research Group. If your business is subscribed to Office 365, this article will acquaint you with the newest features! Automatically Uncover Trends in Excel Data Finding useful information […]